Pages de débordement SQLite : Comment la criminalistique numérique récupère les données cachées
Introduction : Le casse-tête des pages de débordement
Imaginez que vous achetiez une affiche trop grande pour les cadres dont vous disposez chez vous. Pour l'afficher correctement, vous devez le découper en sections afin qu'il tienne dans les cadres disponibles. Le même principe s'applique aux bases de données SQLite lorsqu'elles traitent des enregistrements volumineux : elles les découpent en parties et les stockent sur plusieurs pages. C'est là que pages de débordement viennent.
Les pages de débordement stockent des données qui ne tiennent pas dans une seule page de la base de données SQLite (typiquement 4 096 octets). Ces pages sont liés les uns aux autresLes données de l'analyseur doivent être récupérées dans leur intégralité, formant ainsi une chaîne que l'analyste doit reconstituer. Si les analystes ne respectent pas la structure de débordement, ils risquent de retrouver des preuves incomplètes ou corrompues.
Dans cet article, nous verrons comment fonctionnent les pages de débordement, pourquoi elles sont importantes dans les enquêtes judiciaires et comment extraire des données fragmentées, étape par étape.
Que sont les pages de débordement dans SQLite ?
Les bases de données SQLite allouent une taille de page fixe (par exemple, 4 096 octets). Toutefois, lorsqu'un enregistrement - tel qu'une image stockée sous forme de BLOB (Binary Large Object)-dépasse cette taille, les données excédentaires se déversent dans des pages de débordement.
Principaux enseignements :
✅ Pages de débordement éviter les enregistrements volumineux de monopoliser une seule page.
✅ Ils sont en chaîneà partir de la page principale.
✅ Analystes médico-légaux doit reconstruire ces chaînes pour récupérer des données complètes.
Il est essentiel de comprendre le fonctionnement des pages de débordement pour les enquêtes judiciaires.
Vue d'ensemble : Fonctionnement des pages de débordement
Pour illustrer le concept de pages de débordement, examinons les exemples suivants :
1. Représentation d'images fragmentées

Cette visualisation représente la manière dont les grands BLOB, tels que les images, sont stockés dans SQLite. L'image est divisée en plusieurs sections, tout comme une page de débordement stocke des données fragmentées.
2. Données stockées sur une seule page

Ici, une image tient entièrement dans une page de la base de données, ce qui élimine le besoin de pages de débordement.
3. Données réparties sur plusieurs pages

Cet exemple illustre la façon dont les données sont stockées de manière non contiguë, ce qui nécessite une analyse médico-légale pour les reconstituer correctement.
4. Reconstruction des données à partir des pages de débordement
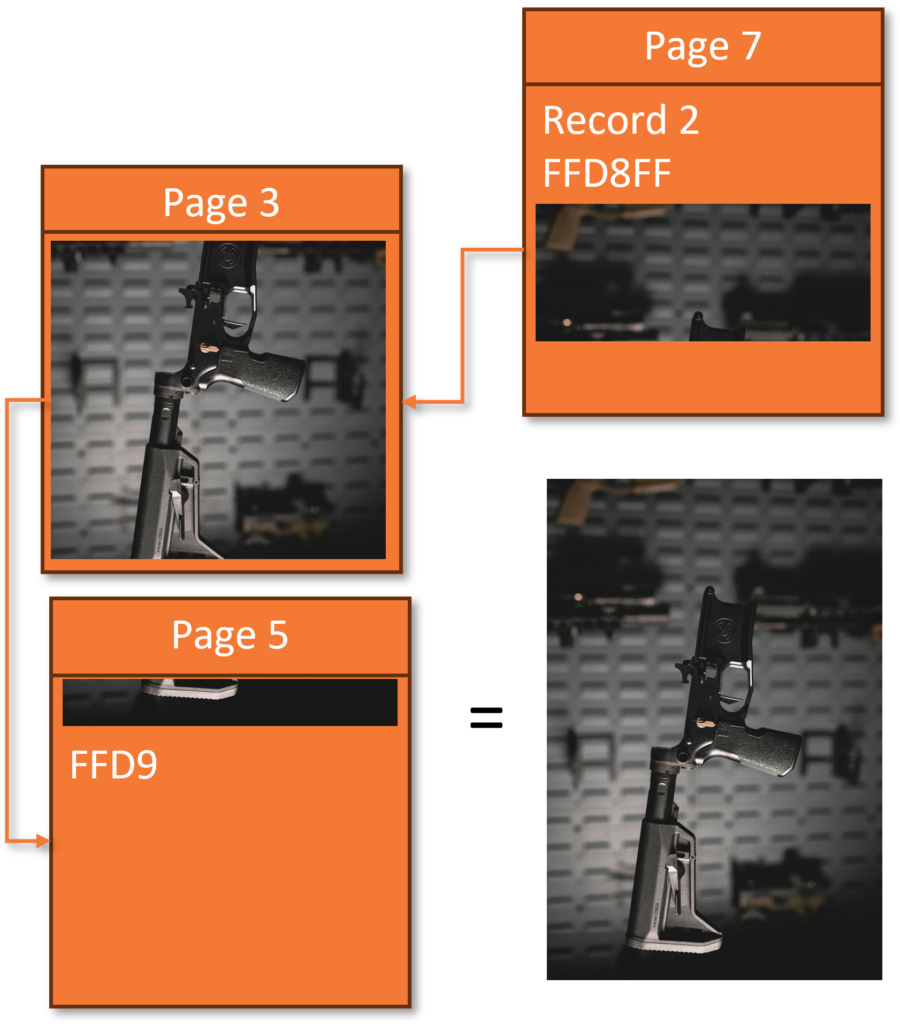
Le suivi des pointeurs de page de débordement permet aux analystes judiciaires de réassembler les données fragmentées.
Importance médico-légale des pages de débordement
Nombreux les applications de messagerie, les applications mobiles et les bases de données stocker les images du profil de l'utilisateur, les journaux de discussion et les pièces jointes dans SQLite. Lorsque les images et les documents s'étendent sur plusieurs pages, les enquêteurs doivent comprendre les structures de débordement pour extraire correctement les données.
Défis médico-légaux :
- Données fragmentées : Les BLOB (tels que les images) sont souvent répartis sur plusieurs pages.
- Récupération basée sur les pointeurs : Les analystes doivent suivre les pointeurs de page de débordement de SQLite pour reconstruire l'image ou le fichier complet.
- Questions relatives à la sculpture : La simple recherche d'un en-tête (FFD8FF) et d'un pied de page (FFD9) JPEG peut échouer parce qu'ils peuvent exister sur des pages distinctes.
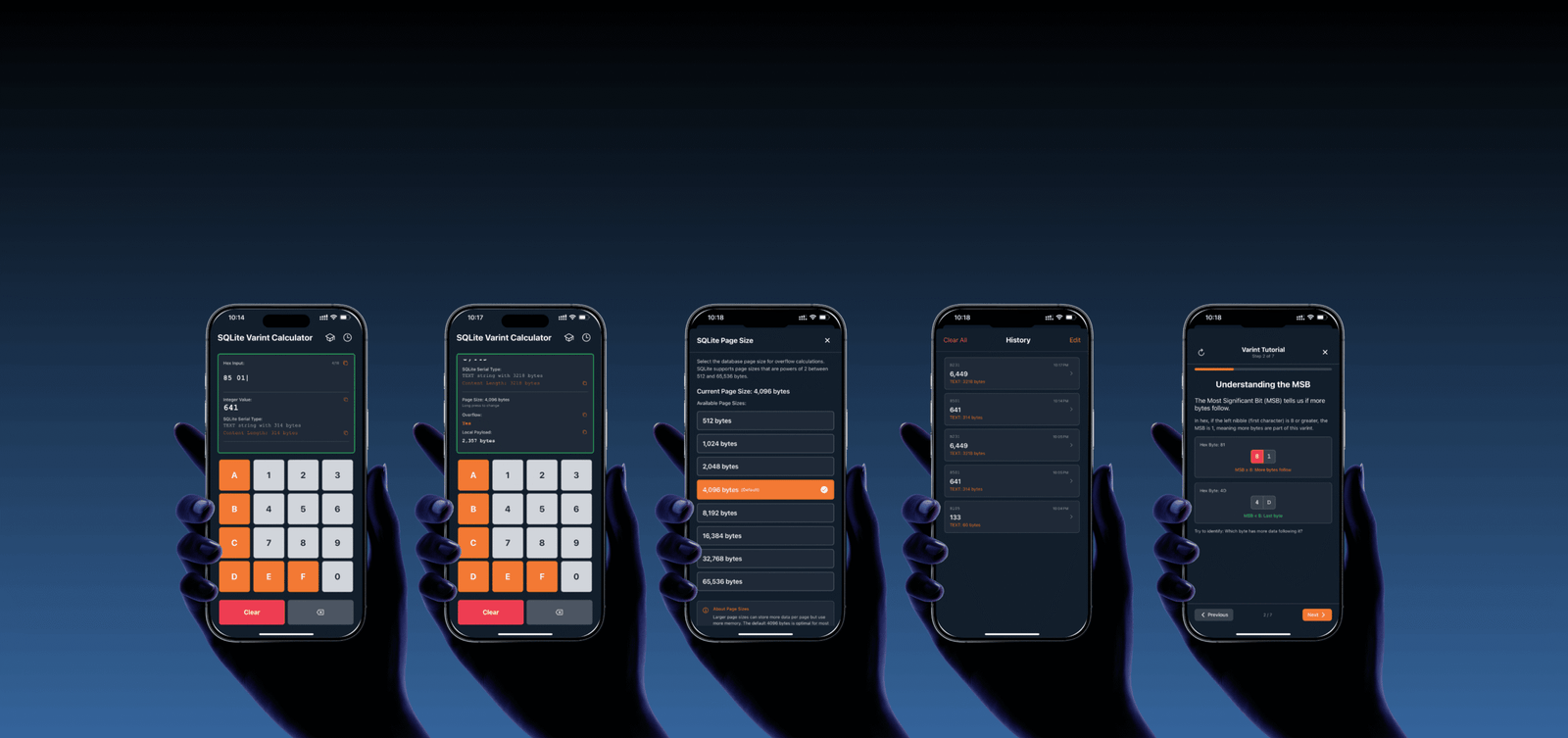
Exemple concret : Extraction d'une image de profil à partir de pages de débordement
Voyons maintenant comment récupérer, étape par étape, une image stockée dans une base de données SQLite.
Localiser le BLOB dans la base de données
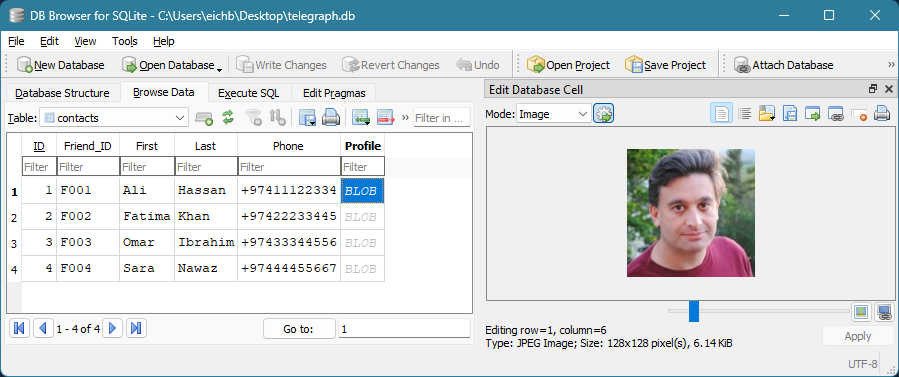
Utilisation DB Browser pour SQLiteLes analystes de la police scientifique identifient l'enregistrement contenant la photo de profil dans la base de données de l'OMPI. contacts table.
Identifier la longueur du BLOB en hexadécimales

Utilisation HxDEn utilisant un éditeur hexagonal, ils localisent l'en-tête de l'enregistrement, qui contient un VARINT qui détermine la longueur du BLOB.
Confirmer la taille de l'image
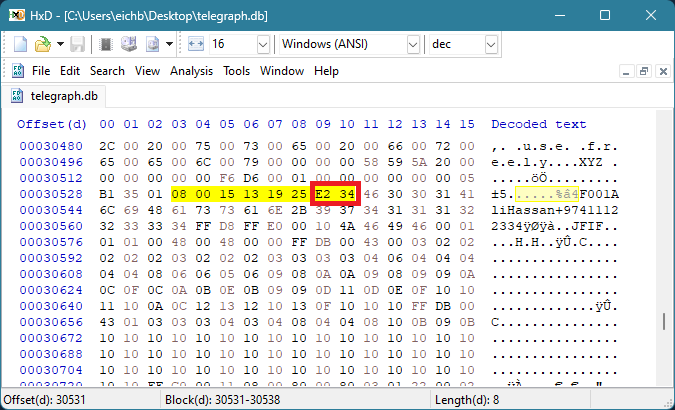
Le deuxième VARINT de l'en-tête de l'enregistrement spécifie la taille de l'image. Dans ce cas, la taille totale est de 6 325 octets, dépassant la limite de pages.
Suivre le pointeur de débordement
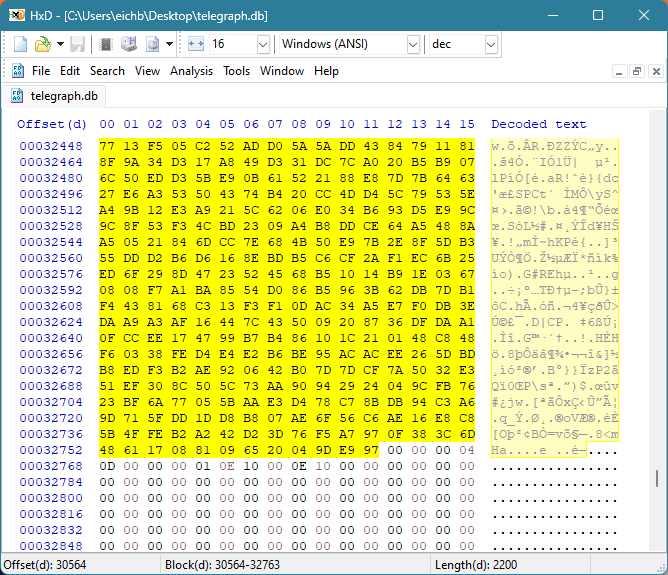
Au bas de la page principale, un pointeur de quatre octets conduit à page 4qui contient la partie suivante de l'image.
Examiner la page de débordement
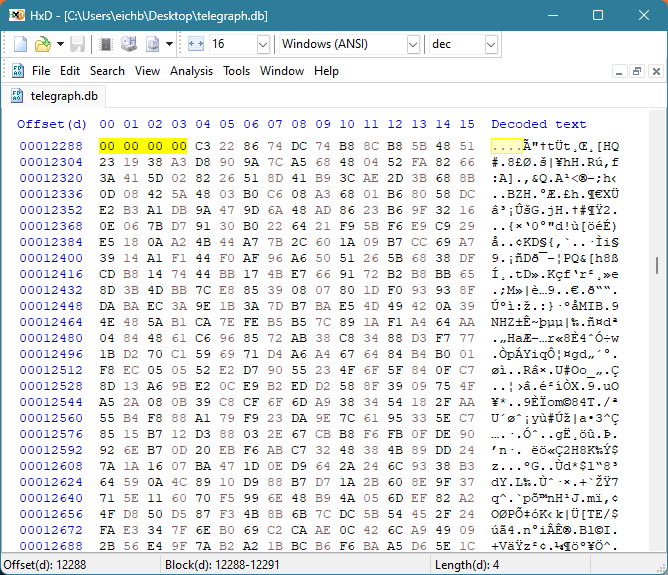
Les quatre premiers octets de la page 4 indiquent si une autre page de débordement suit. Comme la valeur est 0x00000000, il s'agit de la dernière page de débordement.
Extraire et reconstruire l'image
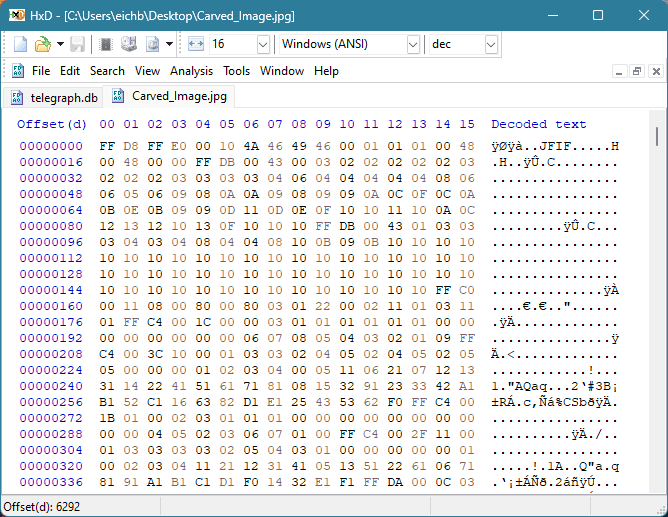
Les analystes judiciaires extraient les 6 292 octets de l'image des deux pages et la reconstruire manuellement.
📌Les pointeurs de quatre octets ne font PAS partie des données à inclure dans l'image sculptée.
Vérifier l'image récupérée

L'image extraite est maintenant entièrement restaurée et visible.
Dernières réflexions : L'importance de l'analyse des pages de débordement
Dans les enquêtes judiciaires, le fait de négliger les pages de débordement peut conduire à perte de preuves critiques. La compréhension du mécanisme de stockage de SQLite est cruciale pour l'extraction et la reconstitution précises des données.
Principales informations médico-légales :
✔️ Toujours vérifier les pages de débordementlors de l'analyse d'enregistrements volumineux.
✔️ Suivre les règles de SQLite pointeurs de débordementavec soin.
✔️ Simple techniques de sculpture à la lime peut ne pas fonctionner en raison d'un stockage non contigu.
Qu'il s'agisse d'analyser les bases de données de chat, les listes de contacts ou les journaux d'applicationLes professionnels de la criminalistique doivent être compétents pour récupérer les données fragmentées.
💡 Avez-vous rencontré des données fragmentées lors d'analyses forensiques de SQLite ? Comment abordez-vous l'analyse des pages de débordement ? Faites-nous part de vos observations ci-dessous !